If you’ve never heard of a Zero-Day Exploit before, you’re not alone. It’s the latest advancement in technology that’s not only remarkable, but threatening to automotive companies and vehicle owners. Hundreds of thousands of Chrysler linked modeled vehicles have been exposed to wireless attacks and will only become even more vulnerable in the next few months.
Andy Greenberg was driving his 2014 Jeep Cherokee at 70 mph in Downtown St. Louis when his vents started blasting cold air. Without him touching the dashboard, the radio turned on, blaring hip-hop music at full volume. He attempted to shut off the air and radio, but he had no control over the features in his vehicle.
As vehicles zoomed passed his Jeep in the middle of the highway, his windshield wipers turned on and fluid blurred his glass.
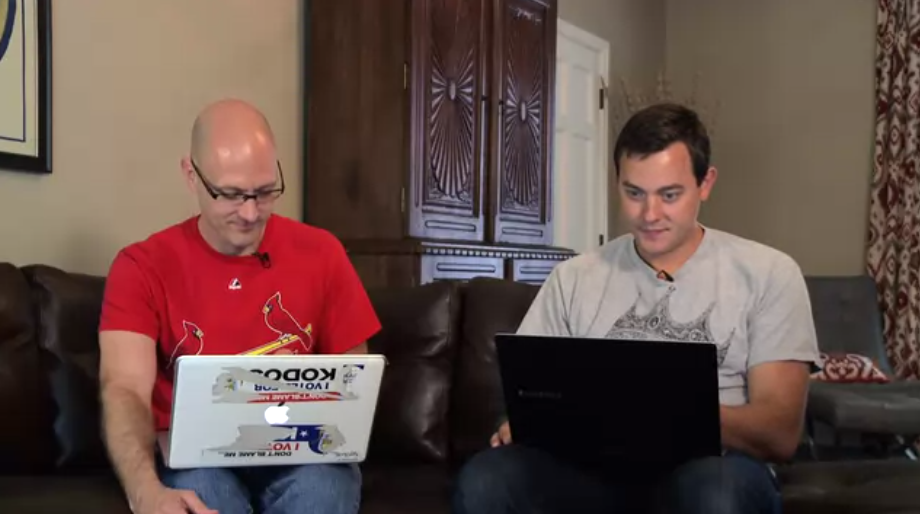
Suddenly, a picture of two men in tracksuits appeared on his vehicle’s digital entertainment display, revealing hackers Charlie Miller and Chris Valasek. While Greenberg was loosing all control of his Jeep Cherokee, these two were back home on their laptops gaining it all.
These three men were undergoing a digital-crash test, a test Greenberg was fully aware of, but to a severity he never anticipated. The hacking technique they used is called Zero-Day Exploit, a technique that targets Jeep Cherokees and allows the attackers to have full wireless control of the vehicle. Hackers send commands through the vehicle’s entertainment system, making it possible for them to control dashboard functions, steering, brakes, and transmission, all through their computer. They have also admitted their full arsenal includes functions that at lower speeds can fully kill the engine, abruptly engage the brakes and even drop pins on a map to trace a vehicle’s route.
They didn’t warn Greenberg of the exact virtual force they’d be using on him. They just told him to drive on the highway and “don’t panic.” What Greenberg bravely endured demonstrates the full control carjackers have on these vehicles.
This isn’t the first time these hackers put Greenberg through such chaos. Back in 2013, when Greenberg was driving his Ford Escape and Toyota Prius around South Bend, Indiana, they sat in the backseat, toying with the car through their laptops. They disabled his brakes, jerked the seat belt and took control of the steering wheel. Back then, they experienced some limitations. At the time, the attackers’s PC had to be wired into the vehicles onboard diagnostic port in order for the hacker to take control of the vehicle.
 Now, hackers managed to advance their technology and have taken carjacking wireless.
Now, hackers managed to advance their technology and have taken carjacking wireless.
Next month, Miller and Valasek plan on making their new technique public, publishing a portion of their exploit on the internet and speaking about it at the Black Hat security conference in Las Vegas.
The only thing keeping carjacking attacks from happening all around the world are two things, according to Wired.com.
“First, they plan to leave out the part of the attack that rewrites the chip’s firmware; hackers following in their footsteps will have to reverse-engineer that element, a process that took Miller and Valasek months. But the code they publish will enable many of the dashboard hijinks they demonstrated on me as well as GPS tracking.
Second, Miller and Valasek have been sharing their research with Chrysler for nearly nine months, enabling the company to quietly release a patch ahead of the Black Hat conference.”
Not surprisingly, the two hackers have shaken up the automative industry and even inspired a new legislation to set new digital security standards for cars and trucks, a challenge hackers embrace without threat.
The Fiat Chrysler Automobile’s is fully committed to providing their costumers with the latest software updates to protect them against vulnerability. A patch must be implemented by a dealership mechanic or a USB stick. Otherwise, Jeeps will likely stay vulnerable to attacks.
The great vulnerability with Chrysler vehicles is only the beginning. In 2011, a team of researchers from the University of Washington and the University of California, San Diego managed to figure out how to wirelessly disable the locks and brakes of a sedan. Researchers of the universities kept the identity of the hacked car secret to the public and only shared the details with carmakers.
There is no doubt that automotive makers need to be fully aware for their vehicle’s digital security. “If consumers don’t realize this is an issue, they should, and they should start complaining to carmakers,” Miller tells Wired.com. “This might be the kind of software bug most likely to kill someone.”
http://video.wired.com/watch/hackers-wireless-jeep-attack-stranded-me-on-a-highway